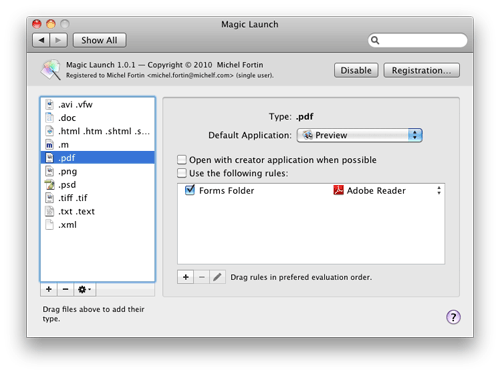
Welcome to a new Apple-world device
So that’s it. The iPad is a small tablet you can carry with you. It has great applications, a great web browser, and the hardware is pretty nice… well I haven’t seen one myself but it looks great. All that at an unbelievably low price. What’s the catch?
Well, it’s a little computer on which you can only install Apple-approved apps, apps you must purchase through the Apple online App Store. No doubt they’ll make a lot of money with the App Store — perhaps that’s how they can afford to sell it at this price — but the point is that everything you buy through the App Store is locked to your specific iTunes account.
What if after some time of use you want to sell your iPad to someone else. That’s fine, you can give him the hardware. But how do you transfer the apps? Those apps are linked to your iTunes account, the same account you use to purchase music, videos, and iPhone apps. You can’t give that account to him, so you’re stuck with apps you can no longer use, nor sell.
As long as it was small, cheap, unessential throwaway apps like you probably have thousands on your iPhone then it doesn’t matter very much. But if you’re going to buy serious apps you’ll want to protect your investment by being able to transfer/sell it to someone else if the need arise. That day the App Store’s DRM will get in your way.
I would also argue, from a developer standpoint, that DRM diminish the value of an app. It’s simple really: DRM prevents your customers from doing things they’d be otherwise legally entitled to do. You could also argue that there’s some privacy implications about purchasing everything through the same outlet, but that’s another subject for another day…
So my conclusion is: I’m pretty sure the iPad will sell, but I’m not sure I want one given the current software ecosystem.
Update: Aristotle Pagaltzis summarize quite well my thought about Apple restricting what you can do with their device.